Implementing Least Privilege IAM Policies for AWS Lambda Functions: A Security Best Practice Guide
AWS Lambda stands out as a foundational service for building serverless applications. Its scalability, cost-efficiency, and operational simplicity have made it a favorite among developers. However, the power and flexibility of serverless also introduce unique security considerations, particularly concerning how your functions interact with other AWS services.
One of the most crucial security best practices for any AWS environment, and especially for serverless architectures, is the principle of least privilege. This principle dictates that an entity (whether it’s a user, role, or application component like an AWS Lambda function) should only have the minimum permissions necessary to perform its intended task, and nothing more.
Implementing least privilege IAM policies for AWS Lambda functions is not just a recommendation; it’s a fundamental requirement for building secure, resilient, and compliant serverless applications. Over-privileged Lambda functions can become a significant attack vector, potentially allowing an attacker to escalate privileges or access sensitive data if the function is compromised.
This comprehensive guide will walk you through the essential concepts, detailed steps, and practical examples for creating secure Lambda functions IAM policies, helping you to optimize your IAM policy for serverless applications and fortify your AWS environment against potential threats.
Understanding IAM Roles and Lambda’s Execution Model
Before diving into policy creation, let’s briefly review how AWS Identity and Access Management (IAM) interacts with Lambda functions.
Every AWS Lambda function executes under an IAM Role, known as the execution role. This role grants the permissions that the Lambda function needs to:
- Read and write logs to Amazon CloudWatch Logs: This is essential for monitoring and debugging your function.
- Access other AWS services: For example, reading from an Amazon S3 bucket, writing to an Amazon DynamoDB table, sending messages to an Amazon SQS queue, invoking other Lambda functions, or interacting with a database hosted on Amazon RDS.
- Access resources within a Virtual Private Cloud (VPC): If your Lambda function needs to access resources (like databases or private APIs) within your Amazon Virtual Private Cloud (VPC), its execution role must have permissions to manage network interfaces (ENIs) within that VPC.
The core challenge lies in defining the exact permissions needed for step 2 and 3, ensuring the function can do its job without unintended access.
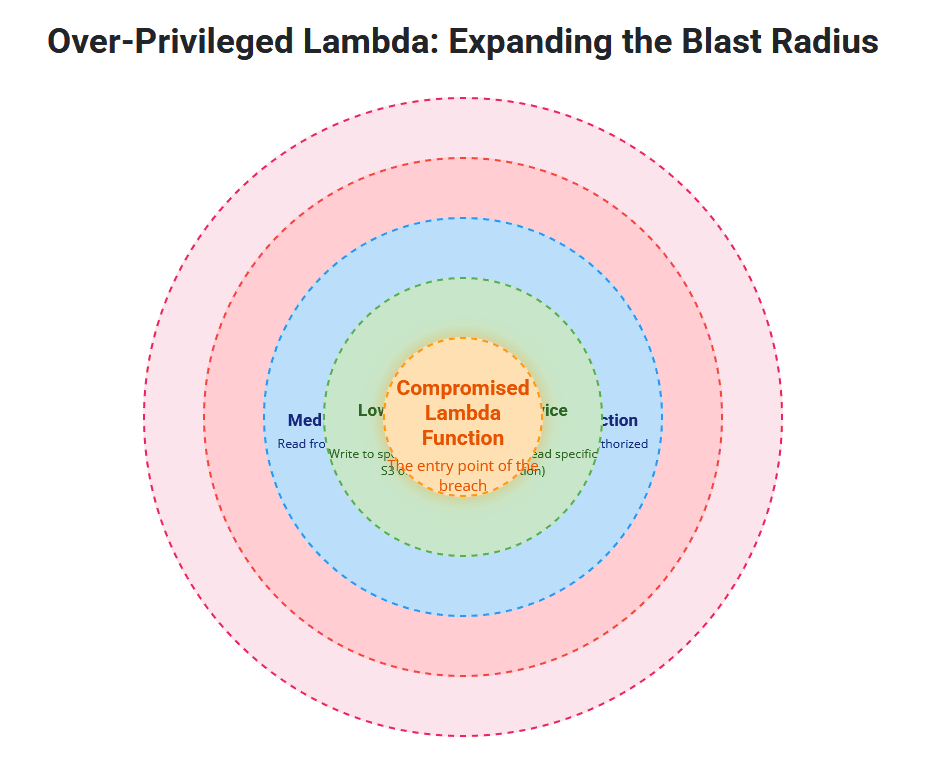
Why Least Privilege is Non-Negotiable for Lambda
The implications of over-privileged Lambda functions are severe:
- Expanded Attack Surface: A compromised function (e.g., via a code injection vulnerability, malicious dependency, or exposed secrets) could be exploited to perform actions beyond its intended scope, leveraging its excessive permissions.
- Data Exfiltration: If a function has
s3:*permissions instead of justs3:GetObjecton a specific bucket, a breach could lead to mass deletion or exfiltration of your entire S3 data. - Privilege Escalation: An attacker might use an over-privileged function to create new IAM users, modify existing policies, or even delete critical resources, leading to a full compromise of your AWS account.
- Compliance Violations: Many regulatory frameworks (e.g., HIPAA, GDPR, PCI DSS) explicitly require the implementation of least privilege, making it a compliance imperative.
- Reduced Auditability: With broad permissions, it becomes harder to trace back malicious activity to a specific intended action versus an unintended exploit.
Core Components of IAM Policies for Lambda
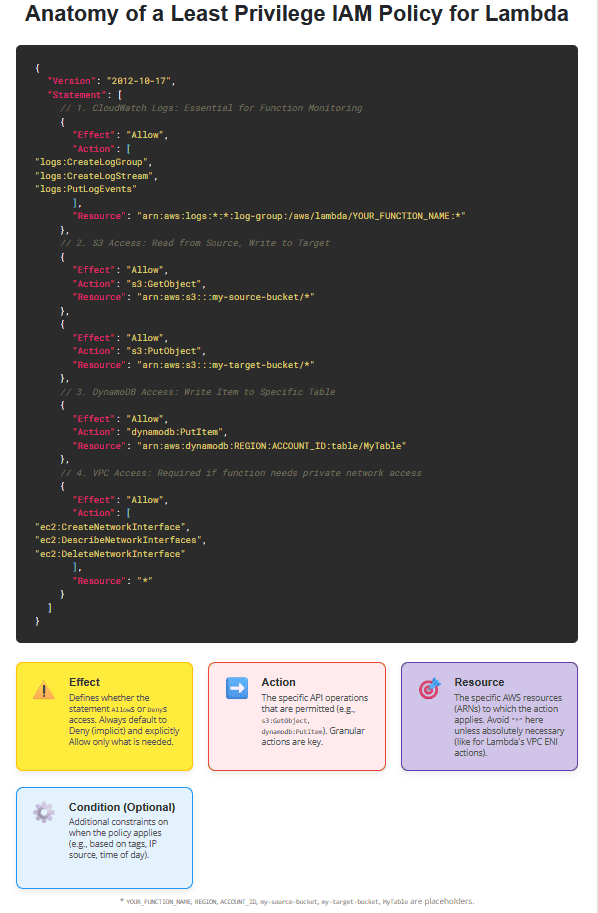
An IAM policy is a JSON document that defines permissions. For Lambda functions, you’ll primarily be working with Identity-Based Policies attached to the Lambda execution role.
A policy consists of one or more statements, each containing:
Effect: Whether the statementAllows orDenys access. Always default toDenyand explicitlyAllowwhat’s needed.Action: The specific API operations that are allowed or denied (e.g.,s3:GetObject,dynamodb:PutItem,sqs:SendMessage).Resource: The AWS resources to which theActionapplies. This is where least privilege is primarily enforced by specifying ARNs (Amazon Resource Names). Using*for resources is a common anti-pattern for least privilege.Condition(Optional): Additional constraints on when the policy applies (e.g., allowing access only from a specific IP address or only if a specific tag is present).
Step-by-Step Guide: Implementing Least Privilege IAM Policies
Let’s walk through the process of building a secure Lambda functions IAM policy.
Step 1: Identify the Function’s Exact Requirements
This is the most critical initial step. Before writing any policy, clearly understand what your Lambda function needs to do. Ask yourself:
- Which AWS services does it interact with? (e.g., S3, DynamoDB, SQS, SNS, SSM Parameter Store, RDS)
- Which specific actions (API calls) does it need to perform on those services? (e.g.,
GetObject,PutItem,SendMessage,DescribeInstances) - Which specific resources (ARNs) does it need to interact with? (e.g., a particular S3 bucket, a specific DynamoDB table, an SQS queue)
- Does it need VPC access? If yes, what subnets and security groups?
- Does it need access to secrets? (e.g., using AWS Secrets Manager or SSM Parameter Store)
Example Scenario: A Lambda function processes images uploaded to an S3 bucket (my-source-images), resizes them, and stores the resized images in another S3 bucket (my-resized-images). It also records metadata about the processed image in a DynamoDB table (ImageMetadataTable).
Step 2: Start with the Absolute Minimum (CloudWatch Logs)
Every Lambda function needs permission to write logs to CloudWatch Logs. This is the baseline.
{
"Version": "2012-10-17",
"Statement": [
{
"Effect": "Allow",
"Action": [
"logs:CreateLogGroup",
"logs:CreateLogStream",
"logs:PutLogEvents"
],
"Resource": "arn:aws:logs:*:*:log-group:/aws/lambda/YOUR_FUNCTION_NAME:*"
}
]
}Explanation:
logs:CreateLogGroup: Allows the function to create its dedicated log group if it doesn’t exist.logs:CreateLogStream: Allows the function to create log streams within its log group.logs:PutLogEvents: Allows the function to write log events to the log stream.Resource: Crucially, we specify the exact log group for this function:/aws/lambda/YOUR_FUNCTION_NAME. ReplaceYOUR_FUNCTION_NAMEwith the actual name of your Lambda function. This prevents the function from writing logs to other log groups or creating arbitrary ones.
Step 3: Add Permissions for Required Services and Specific Resources
Based on our example scenario, the function needs S3 and DynamoDB permissions.
S3 Permissions:
- Action:
s3:GetObjectonmy-source-images - Action:
s3:PutObjectonmy-resized-images
{
"Version": "2012-10-17",
"Statement": [
{
"Effect": "Allow",
"Action": [
"logs:CreateLogGroup",
"logs:CreateLogStream",
"logs:PutLogEvents"
],
"Resource": "arn:aws:logs:*:*:log-group:/aws/lambda/YOUR_FUNCTION_NAME:*"
},
{
"Effect": "Allow",
"Action": "s3:GetObject",
"Resource": "arn:aws:s3:::my-source-images/*"
},
{
"Effect": "Allow",
"Action": "s3:PutObject",
"Resource": "arn:aws:s3:::my-resized-images/*"
}
]
}Explanation:
- We use
arn:aws:s3:::my-source-images/*to allow reading only from objects within themy-source-imagesbucket. - We use
arn:aws:s3:::my-resized-images/*to allow writing only to objects within themy-resized-imagesbucket. - Notice the
/*at the end of the S3 bucket ARNs. This is critical for object-level permissions. Without it, you’re only granting permissions at the bucket level (e.g.,s3:ListBucket), not for the objects within it.
DynamoDB Permissions:
- Action:
dynamodb:PutItemonImageMetadataTable
{
"Version": "2012-10-17",
"Statement": [
{
"Effect": "Allow",
"Action": [
"logs:CreateLogGroup",
"logs:CreateLogStream",
"logs:PutLogEvents"
],
"Resource": "arn:aws:logs:*:*:log-group:/aws/lambda/YOUR_FUNCTION_NAME:*"
},
{
"Effect": "Allow",
"Action": "s3:GetObject",
"Resource": "arn:aws:s3:::my-source-images/*"
},
{
"Effect": "Allow",
"Action": "s3:PutObject",
"Resource": "arn:aws:s3:::my-resized-images/*"
},
{
"Effect": "Allow",
"Action": "dynamodb:PutItem",
"Resource": "arn:aws:dynamodb:REGION:ACCOUNT_ID:table/ImageMetadataTable"
}
]
}Explanation:
dynamodb:PutItem: Allows the function to add new items to the table.Resource: The full ARN for the specific DynamoDB table. Remember to replaceREGIONandACCOUNT_IDwith your AWS region and account ID.
Step 4: Add VPC Execution Permissions (If Required)
If your Lambda function needs to connect to resources within a VPC (e.g., an RDS database instance, a private API), you must grant it permissions to manage network interfaces.
{
"Version": "2012-10-17",
"Statement": [
... (previous statements) ...
{
"Effect": "Allow",
"Action": [
"ec2:CreateNetworkInterface",
"ec2:DescribeNetworkInterfaces",
"ec2:DeleteNetworkInterface"
],
"Resource": "*"
}
]
}Explanation:
- The
ec2:CreateNetworkInterface,ec2:DescribeNetworkInterfaces, andec2:DeleteNetworkInterfaceactions are required for Lambda to attach an Elastic Network Interface (ENI) to your function’s execution environment within your VPC. - Important: For these specific EC2 actions related to ENI management by Lambda, the
Resourcemust be*. This is one of the rare exceptions to the “avoid*in Resource” rule, as Lambda needs permission to create ENIs across subnets/security groups it’s configured for within your VPC. However, ensure the context of these permissions is strictly for ENI creation by Lambda.
Step 5: Attach the Policy to the Lambda Execution Role
- Create an IAM Role: If you haven’t already, create a new IAM role with the
lambda.amazonaws.comservice as the trusted entity. This allows Lambda to assume this role.- In the IAM Console, go to Roles, click Create role.
- Select AWS service -> Lambda. Click Next.
- Attach the Policy:
- In the “Add permissions” step, you can either:
- Create a new custom policy (recommended for true least privilege): Go to the JSON tab and paste your constructed policy. Save it with a descriptive name (e.g.,
MyImageProcessorLambdaPolicy). Then search for and attach this policy. - Attach an existing managed policy (less granular): Not ideal for least privilege, but useful for basic needs. For example,
AWSLambdaBasicExecutionRolecovers just CloudWatch Logs.
- Create a new custom policy (recommended for true least privilege): Go to the JSON tab and paste your constructed policy. Save it with a descriptive name (e.g.,
- In the “Add permissions” step, you can either:
- Review and Create Role: Give your role a descriptive name (e.g.,
LambdaImageProcessorExecutionRole) and create it. - Assign Role to Lambda Function: When you create or update your Lambda function, select this newly created IAM role as its Execution role.
Advanced Least Privilege Techniques for Lambda
- Using Resource Tags in Policies:
- Tag your AWS resources (e.g.,
Environment:Production,Project:ImageProcessing). - Use conditions in your IAM policy to grant permissions only if a resource has a specific tag. This is incredibly powerful for scaling least privilege across many resources.
- Tag your AWS resources (e.g.,
{
"Effect": "Allow",
"Action": "s3:GetObject",
"Resource": "arn:aws:s3:::*",
"Condition": {
"StringEquals": {
"s3:ExistingObjectTag/Project": "ImageProcessing"
}
}
}This policy would allow s3:GetObject on any S3 object that has a tag Project with the value ImageProcessing.
- Service Control Policies (SCPs) with AWS Organizations:
- If you’re using AWS Organizations, SCPs can act as guardrails, setting maximum permissions for accounts within your organization. While not specific to a Lambda function, they can prevent the creation of overly permissive IAM roles in the first place.
- IAM Access Analyzer:
- Leverage IAM Access Analyzer to identify resources shared externally or to validate your IAM policies against the principle of least privilege. It can help identify unintended public or cross-account access.
- AWS Config Rules:
- Set up AWS Config rules to proactively detect and flag non-compliant resources, such as Lambda functions with overly permissive roles.
- AWS Secrets Manager and SSM Parameter Store:
- Never hardcode sensitive information (API keys, database credentials) in your Lambda code or environment variables.
- Use AWS Secrets Manager or SSM Parameter Store (SecureString) to store secrets securely. Your Lambda function’s IAM role then only needs
secretsmanager:GetSecretValueorssm:GetParameterspermissions for specific secret/parameter ARNs.
- Context Keys in Conditions:
- Use global condition context keys (e.g.,
aws:SourceVpc,aws:SourceIp) to restrict actions further based on the invocation context. For example, allow S3 uploads only if the request originated from a specific VPC endpoint.
- Use global condition context keys (e.g.,
- Monitoring with CloudTrail and CloudWatch:
- Enable AWS CloudTrail to log all API calls made in your AWS account. This provides an audit trail of actions taken by your Lambda functions (via their roles).
- Create CloudWatch Alarms based on CloudTrail logs for suspicious activities (e.g., a
DeleteBucketaction from a function that should only be writing).
Common Anti-Patterns to Avoid
Action: "*": Granting all actions on a service. This is a massive security risk.Resource: "*"(where specific ARNs are possible): Allowing access to all resources of a given type when the function only needs one or a few.- Using AWS Managed Policies that are too broad: While convenient, policies like
AmazonS3FullAccessare almost never appropriate for a Lambda function’s execution role. Create custom policies instead. - Hardcoding Secrets: Storing API keys or database credentials directly in code or environment variables is a major vulnerability.
- Overlooking Triggers and Downstream Services: Remember to secure the permissions for your Lambda function’s triggers (e.g., S3 putting objects into Lambda, API Gateway invoking Lambda) and any downstream services it might invoke. These are separate IAM concerns, but equally important.
👉 Ask our Educational Tutor now!
Conclusion: Fortifying Your Serverless Security Posture
Implementing least privilege IAM policies for AWS Lambda functions is a cornerstone of robust serverless security. It’s a continuous process that requires a thorough understanding of your function’s operational needs and a commitment to meticulous policy crafting.
By adhering to the principles outlined in this guide – identifying precise requirements, starting with minimal permissions, specifying granular actions and resources, and leveraging advanced IAM features – you can secure Lambda functions IAM effectively. This proactive approach not only minimizes your attack surface and reduces the blast radius in the event of a compromise but also significantly optimizes your IAM policy for serverless applications, leading to a more secure, compliant, and well-governed AWS environment. Make least privilege a non-negotiable standard in your serverless development lifecycle.



